In the graphic below, the military's Office of Information Awareness has
illustrated their plan for a Total Information Awareness System. Near the
center of the graphic is a red dotted line labeled "Privacy and Security."
The line represents a computer algorithm, and may represent other means,
for preventing the "Transactional Data" at the left of the illustration
from being used in a way that violates an individual or group's "privacy
and security." The "transactional data" includes information about finances,
healthcare, education, and other important personal information. The idea
is that this information will not reach the "multi-agency analytical environment"
unless it passes the standards set for privacy and security, so people's
personal information will be protected. |
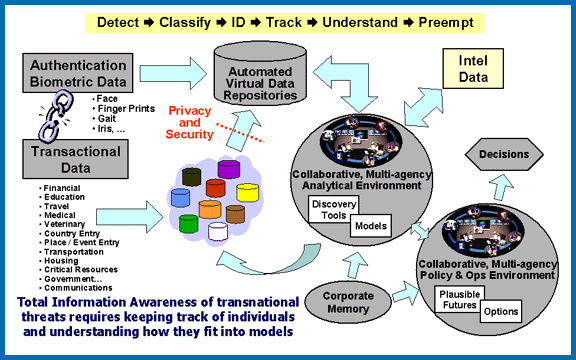 |
The first objection
to such a setup is that it is impossible to protect an individual or group's
privacy and security using an algorithm or other means, because any protection
will reflect the opinions of the politicians, government employees, and
analysts that set the standards for the algorithms or other protections.
However, this chart actually contains a flaw that reveals how, even in a
simple model, information can slip past protective systems. In this model,
the "Privacy and Security" line is essentially useless. It is,
of course, not clear whether or not this mistake is intentional, but the
error shows the danger such a system poses for the privacy and security
of the public. And it shows that the people in charge of protecting our
privacy and security are not going to be able to deliver what they promise
if this chart is evidence of their analytical skill.
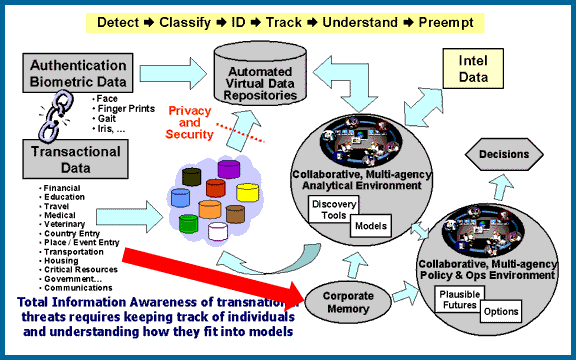
In the graphic below, a red line has been added to show the error. The "Transactional
Data" never passes through the "Privacy and Security" line.
Most of the "Transactional Data" is already available in the oval
labeled "Corporate Memory." Information about an individual's
finances, healthcare, education, and other important personal information
is already available through corporate systems, such as banks and credit
card companies, retailers, hospitals and doctor's offices, insurers, universities
and student loan companies, and other corporate sources. |
 |
|
The presentation entitled Why Should You Care
if the Government Spies on You? discusses how Total Information
Awareness can be abused by leaders in order to suppress political dissent
and frighten people who challenge their government. That is reason enough
to abandon such a project. But the kinds of colossal errors made at the
program's inception threaten privacy and security even more. Not only
is it impossible to protect privacy and security in such a system due
to the opinions of those charged with the duty, it is impossible to guard
against errors that will inevitably lead to abuses of such a system. The
errors in this chart alone indicate that the people in charge of protecting
our privacy and security are not up to the job, and depending on the nature
of the mistake, may actually be seeking to undermine privacy and security
altogether. The "Privacy and Security" line is useless in this chart,
and Americans should not trust their privacy to the people that drew it.
|
|
|
| If
this presentation has you asking questions, check out NewsKing.com
for additional articles and presentations, as well as links
to neoNewton.com
and other sites where answers are waiting! Click HERE
to visit NewsKing.com! |
 |
|
|
|
|
© Copyright 1998-2003 T.J. Newton. Click HERE
to read the terms and conditions of copyright. All rights reserved.
|





